<span id="top"></span>
Configuring OneLogin SSO
This guide outlines the steps to configure Single Sign-On (SSO) with OneLogin for Qualified. Follow these instructions to streamline authentication for your users and enhance security.
- Prerequisites
- Steps to Configure OneLogin SSO
- Enable SCIM Provisioning (Optional)
- Binding Email Process for Existing Users
- Adding New Users
- Disconnecting SSO
<span id="prerequisites"></span>
Prerequisites
- Access to OneLogin as an Account Owner, or as a user with Super User or Manage App privileges.
- Access to Qualified’s Enterprise Single Sign-on, and the Admin user role.
- Your organization’s Company ID from Qualified.
- A basic understanding of SAML 2.0 configuration.
<span id="steps-to-configure"></span>
Steps to Configure OneLogin SSO
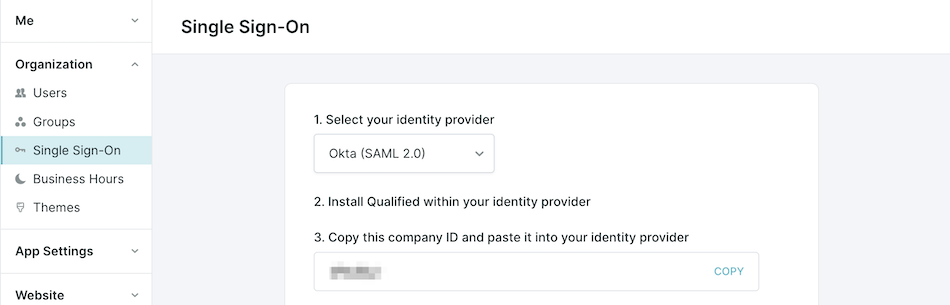
Step 1: Set up in Qualified
- Log in to your Qualified Admin account.
- Navigate to Settings → Organization → Single Sign-On.
- Select OneLogin (SAML 2.0) from the dropdown menu.
- Copy your Company ID.
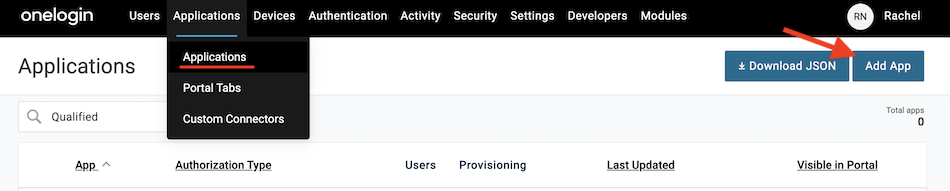
Step 2: Configure in OneLogin
- Log in to the OneLogin Admin Console
- Go to Applications → Applications and click Add App.
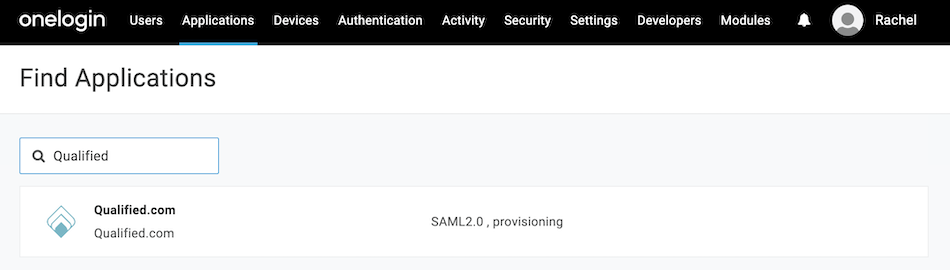
- Search for “Qualified” to find our application and select it.
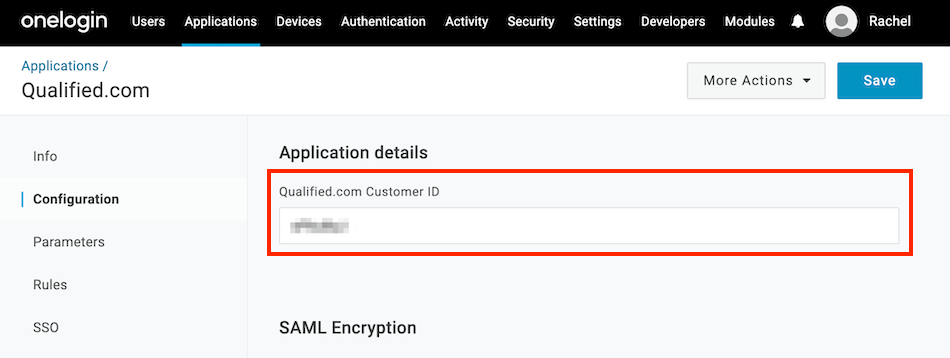
- Click Save to display additional configuration tabs.
- Under the Configuration tab, enter the Company ID you copied from your Qualified account to the Application Details and Save.
- Next, click More Actions, then right-click on SAML Metadata, and select Copy link address. You’ll add this link in Qualified in just a moment.
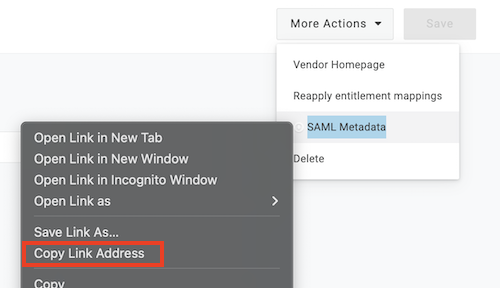
- Lastly, assign the application to yourself to complete the configuration.
OneLogin Documentation: Introduction to App Management
Step 3: Finalize SSO in Qualified
- Return to Settings → Organization → Single Sign-On in Qualified.
- Paste the SAML Metadata link you copied from OneLogin into the required field, and click Save.
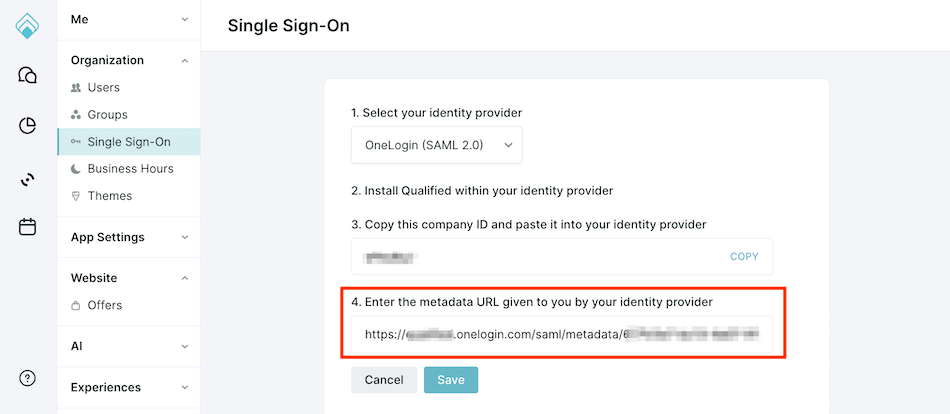
- Click Verify Configuration to test the connection.
- Before enabling single sign-on, make sure to assign all existing Qualified users access to the Qualified application in OneLogin as they will no longer be able to access Qualified with their password once SSO is enabled.
- Existing users will receive an email to bind their accounts: Binding Email Process for Existing Users
- When you’re ready, click Enable single sign-on for this org.
<span id="enable-scim-provisioning"></span>
Enable SCIM Provisioning (Optional)
SCIM provisioning automates user creation, updates, and deactivation directly from OneLogin. This step is optional but highly recommended for efficient user management.
Supported Provisioning Features
The following provisioning features are supported within Qualified provisioning of SSO users:
- Push New Users: New users created through OneLogin will also be created in Qualified.
- When a user is provisioned, their name, role, phone number, email, and timezone from OneLogin are synced to Qualified. Further updates are limited to email and role changes only.
- Push Profile Updates: Updates made to a user's email or role in OneLogin are pushed to Qualified.
- Push User Deactivation: Deactivating a user or disabling their access to the Qualified application in OneLogin will deactivate the user in Qualified.
- Deactivation removes login access but retains the user's information in Qualified as inactive.
- Reactivate Users: User accounts can be reactivated in Qualified via OneLogin.
Unsupported Provisioning Features
The following features are not supported:
- Import Users
- Import/Push Groups
- Sync Password
- Profile Sourcing
Steps to Enable SCIM Provisioning
Step 1: In Qualified
- Go to Settings → Organization → Single Sign-On.
- Toggle on SCIM Enabled to enable SCIM provisioning.
- Copy the SCIM OAuth Bearer Token displayed on the screen.
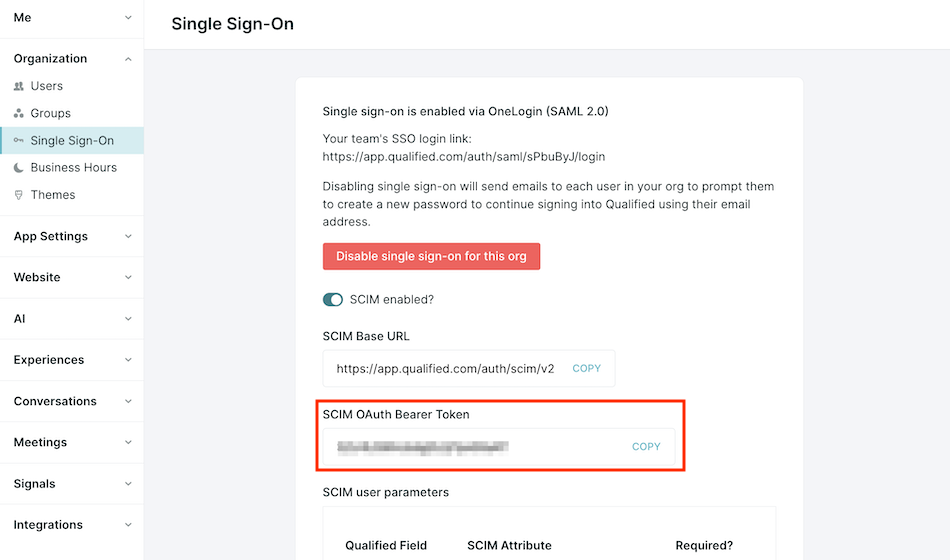
Step 2: In OneLogin
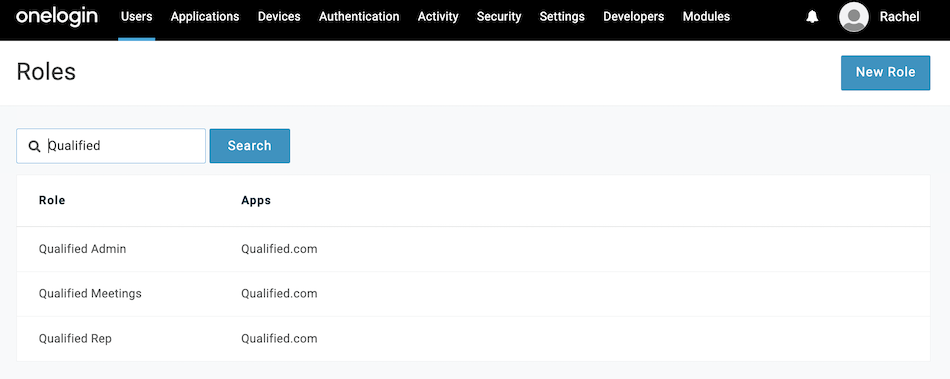
- In your OneLogin Admin console, go to Users → Roles and create the following roles, and add access to the Qualified app:
- Qualified Admin
- Qualified Rep
- Qualified Meeting
OneLogin Documentation: Creating Roles
- Next, go to Applications → Applications, find the Qualified application, and click to open it.
- Navigate to the Configuration tab.
- Enable the API Connection.
- Paste the SCIM OAuth Bearer Token from Qualified into the SCIM Bearer Token field, and Save.
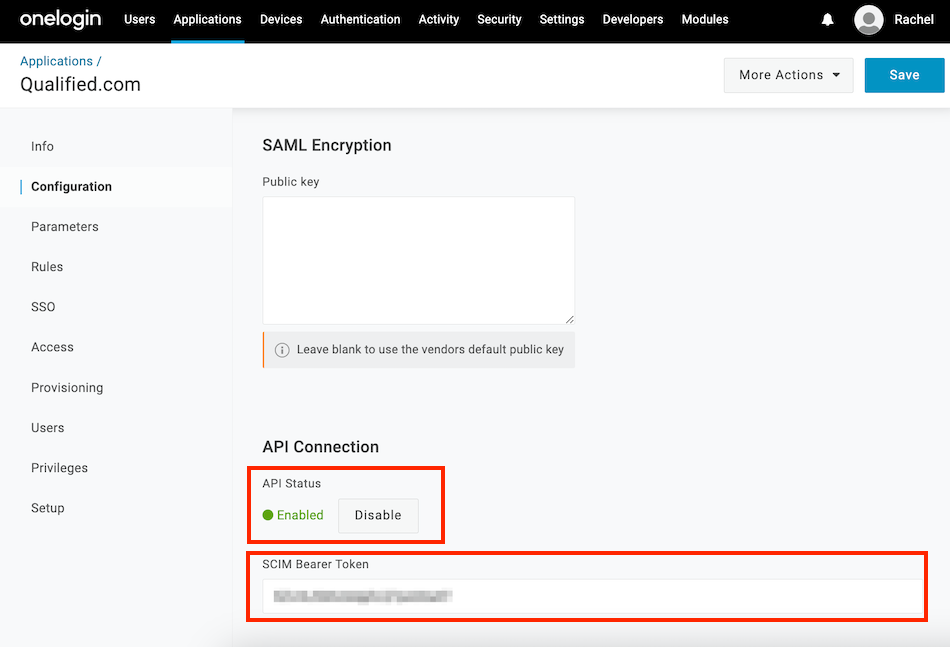
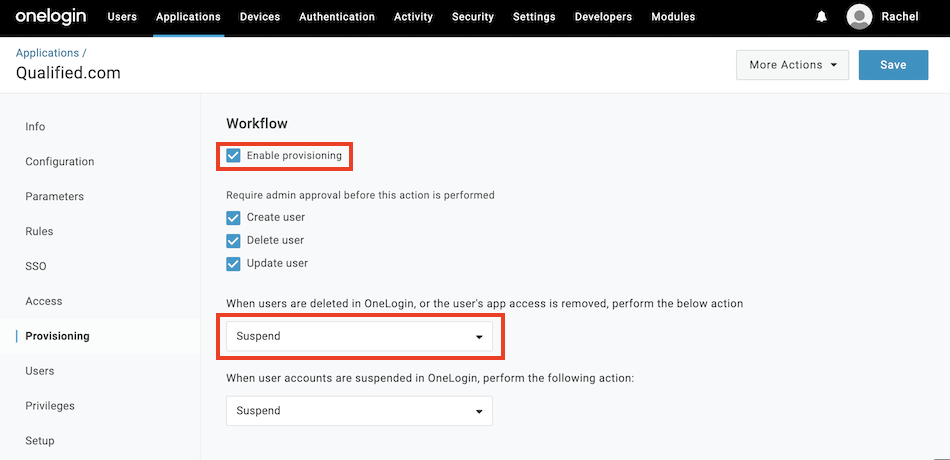
- Next, go to to the Provisioning tab.
- Check the box to Enable Provisioning.
- Under "When users are deleted in OneLogin, or the user's app access is removed," select Suspend. Then, click Save.
- Navigate to the Rules tab.
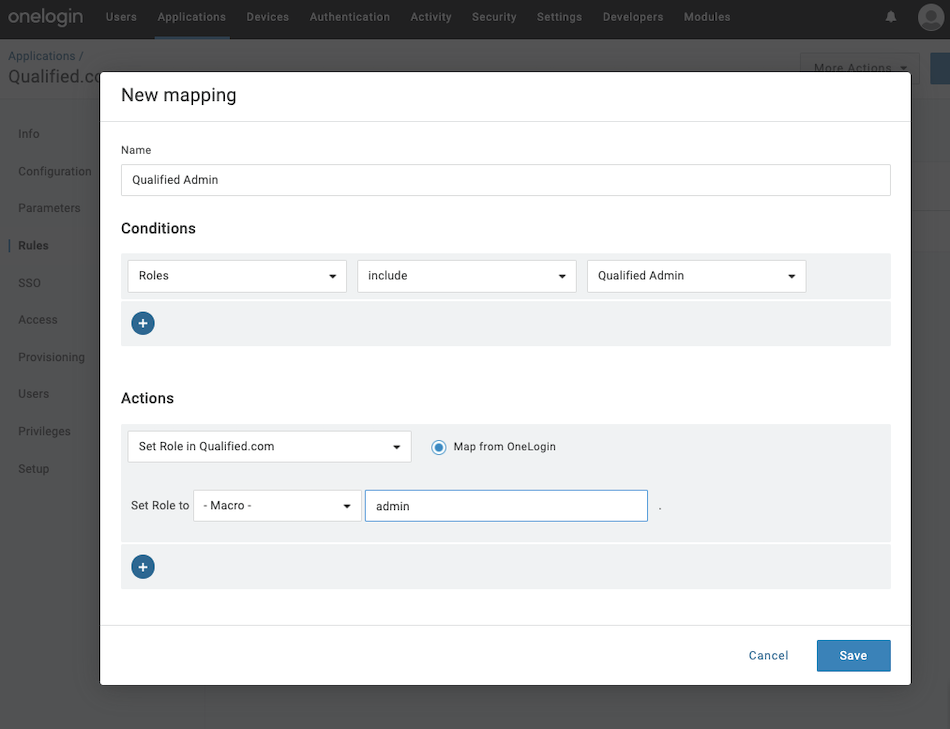
- Click Add Rule to create the first of three rules, one for each Qualified Role:
- Name: Qualified Admin
- Conditions: Roles → include → Qualified Admin
- Actions: Set Role in Qualified.com (check box “Map from OneLogin” → Set Role to “-Macro-” → admin
- Click Save.
- Click Add Rule to create the first of three rules, one for each Qualified Role:
- Create another Rule for Qualified Rep (set Role to “rep”)
- Create another Rule for Qualified Meetings (set Role to “meetings”)
OneLogin Documentation: Configuring Apps
Testing and Verification
- Add a test user in OneLogin:
- Assign the user one of the roles you created (e.g., Qualified Admin, Qualified Rep, Qualified Meetings).
- Verify the user is created in Qualified with the correct attributes and role.
- Update the test user's attributes (e.g., email or role) in OneLogin:
- Confirm the changes sync correctly in Qualified.
- Deactivate the test user in OneLogin:
- Ensure the user’s access is removed in Qualified while their profile remains inactive.
<span id="binding-email-process"></span>
Binding Email Process for Existing Users
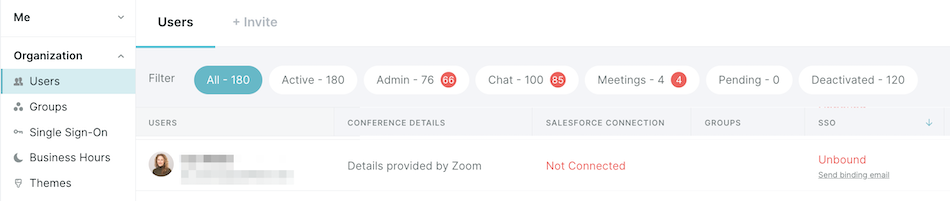
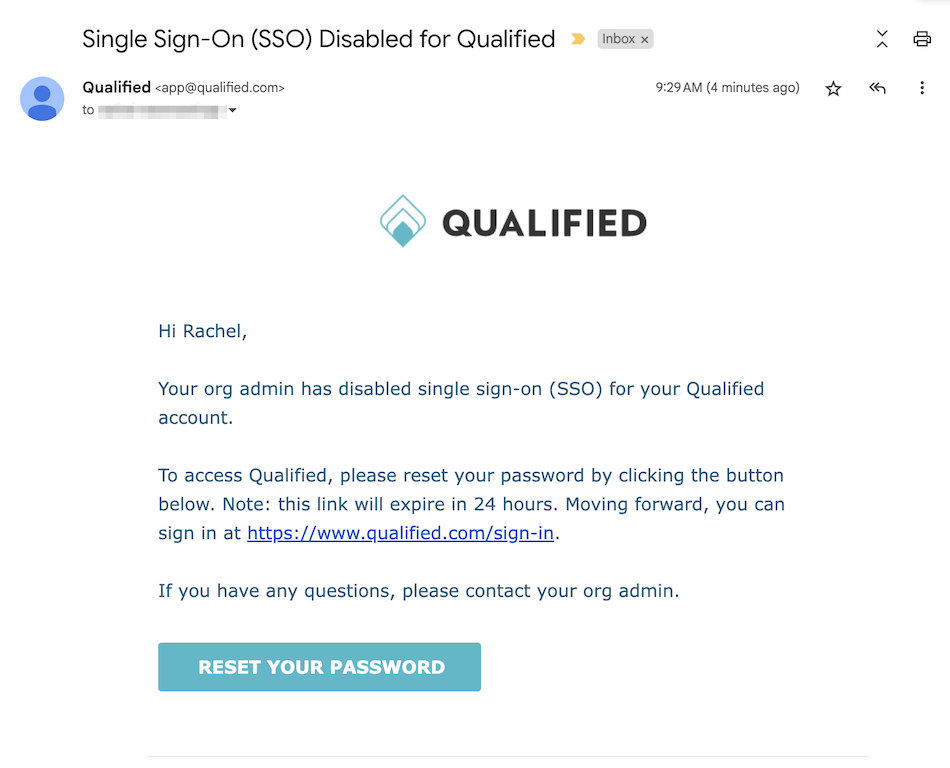
After enabling SSO, all existing Qualified users receive an email from app@qualified.com with a unique binding link.
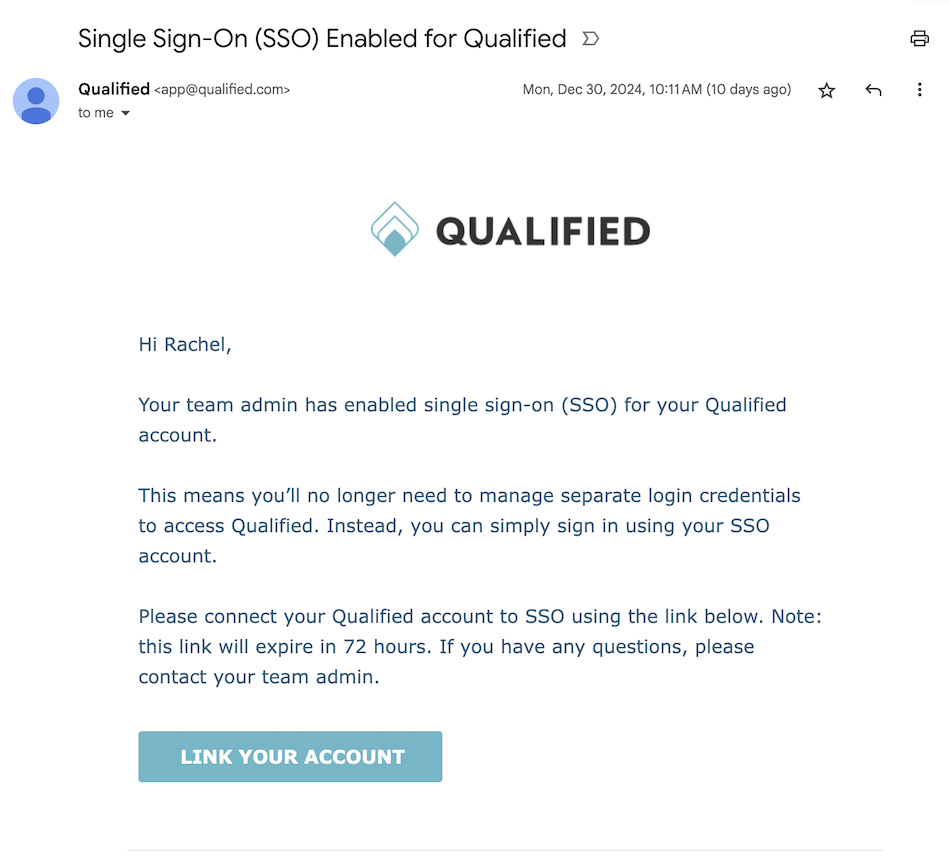
Users must click the link within 72 hours to bind their Qualified account to their OneLogin Account. If the binding link expires, an admin can resend it from Qualified by going to Settings → Organization → Users.
<span id="adding-new-users"></span>
Adding New Users
With SCIM Provisioning Enabled
A OneLogin user with Super user, or have the Manage Role privilege to the Qualified roles, will need to assign the user to the appropriate Qualified Role to add them to Qualified.
OneLogin Documentation: Assigning Roles to Users
Without SCIM Provisioning
If your company does not have SCIM Provisioning enabled, then you’ll follow the steps below to add new users to Qualified:
- Assign Users in OneLogin: A OneLogin admin with Super user, Manage user, or Manage application privileges will need to assign the user to the Qualified application: Manually Assigning Apps to Users
- Invite Users in Qualified: Invite users from Settings → Organization → Users in Qualified: Provisioning Users in Qualified
- User Accepts Invite: Invited users will receive an email with a button to link their account and access Qualified.
<span id="disconnecting-sso"></span>
Disconnecting SSO
If you'd like to disconnect your company’s SSO, you can do so at any time.
- Go to Settings → Organization → Single Sign-On
- Click Disable SSO for this team.
- Users will receive an email to create a new password and log in using their email addresses.
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- asdfasdf
- asdfasdf
- asdfasdf
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript
|
|---|
|




.svg)



